The Last Fortress has fallen
What was once secure, is no longer safe.
AI-driven threats, cyber attacks, and quantum advances are breaking through legacy defenses. Even previously secure networks like critical infrastructures are suddenly at risk.
Amidst this shift, a new project takes shape:
Security Sphir – From Regular Firewalls to Quantum Safety
We build something more than just isolated security products. We create a modular, layered security sphere tailored for critical infrastructure.
We call it Sphir: a next-generation security framework, combining software-defined agility, industrial hardening, and quantum-resilient protection.
Why Are Traditional Firewalls Failing?
There was a time when network security was like a fortress. Walls were high, gates well-guarded, and firewalls decided who could come in or out. It worked, when threats were loud, obvious, and outside. But today’s threats are smarter. Faster. Already inside.
Imagine a small, modern data packet, sleek, encrypted, and cloud-native, approaching the edge of your network. The firewall doesn’t challenge it. It doesn’t even blink. In fact, it holds the door open.
Why? Because the old rules no longer apply. Legacy firewalls were built for a different era. They’re:
These outdated tools weren’t designed for what networks have become: dynamic, distributed, and decentralized.
And the cost? Fragmented defenses, higher risk, and cracks in even the most critical infrastructures.
The Problem We Solve
Security is no longer optional. It’s the foundation of operational sovereignty.
From energy grids to train stations, from telecom nodes to sovereign data flows – every environment has different needs. But traditional security stacks are rigid, complex, and not designed for critical infrastructure. Security shouldn’t slow you down, it should scale with you.
Consider these facts:
The average cost of a critical infrastructure breach was $4.82 million in 2023, according to IBM.
71% of utilities surveyed by the European Union Agency for Cybersecurity (ENISA) reported increased attacks targeting OT networks.
The “Store now, decrypt later” (SNDL) threat is real: data exfiltrated today may be decrypted once quantum computing reaches maturity.
That’s why we created Sphir: to deliver the right protection, right where it matters. Now and in the future.
Security Sphir Framework
One modular framework. Three focused solutions, combining software-defined agility, industrial hardening, and quantum-resilient protection.

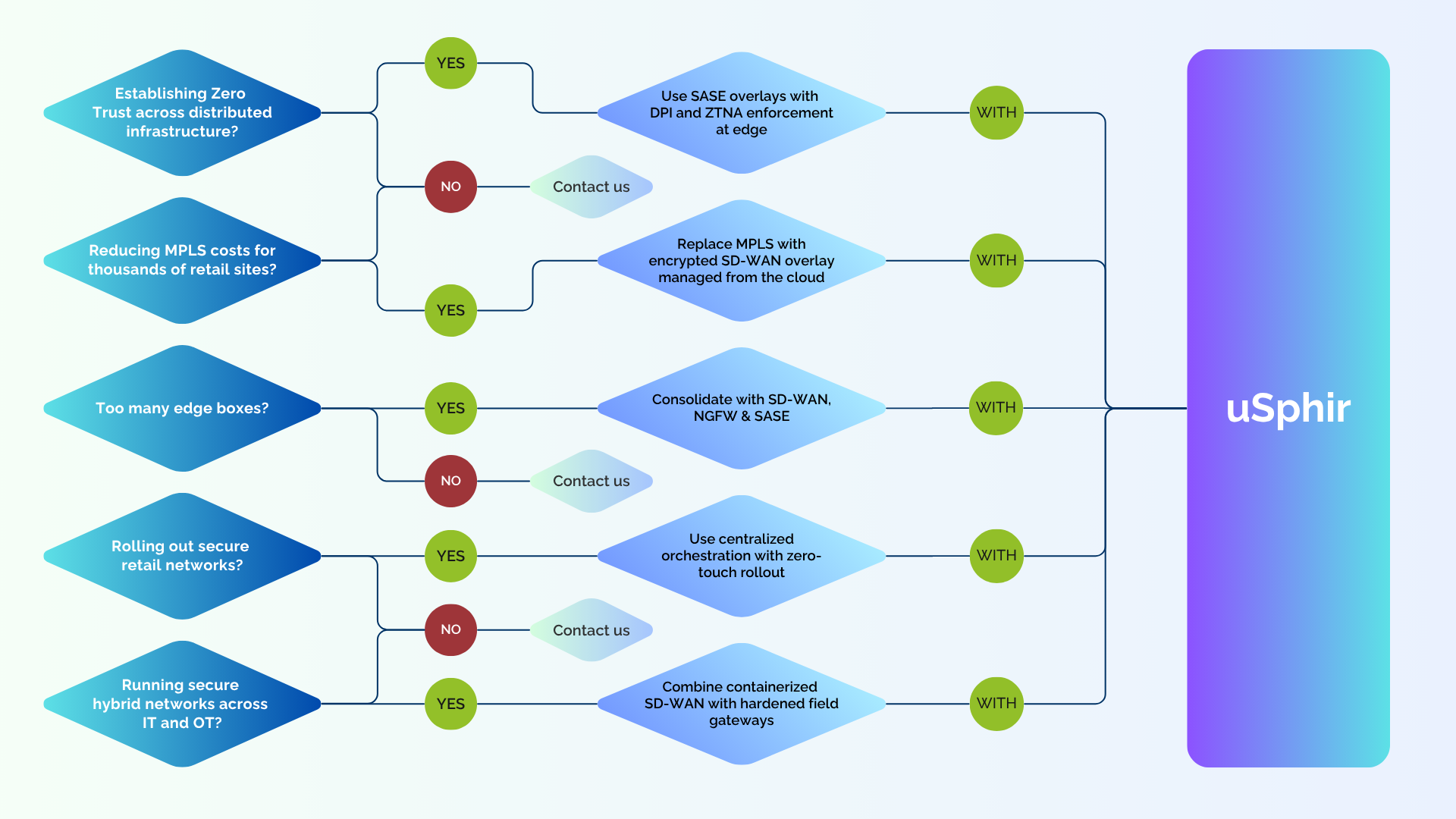
uSphir
Universal security: software-defined protection at the edge

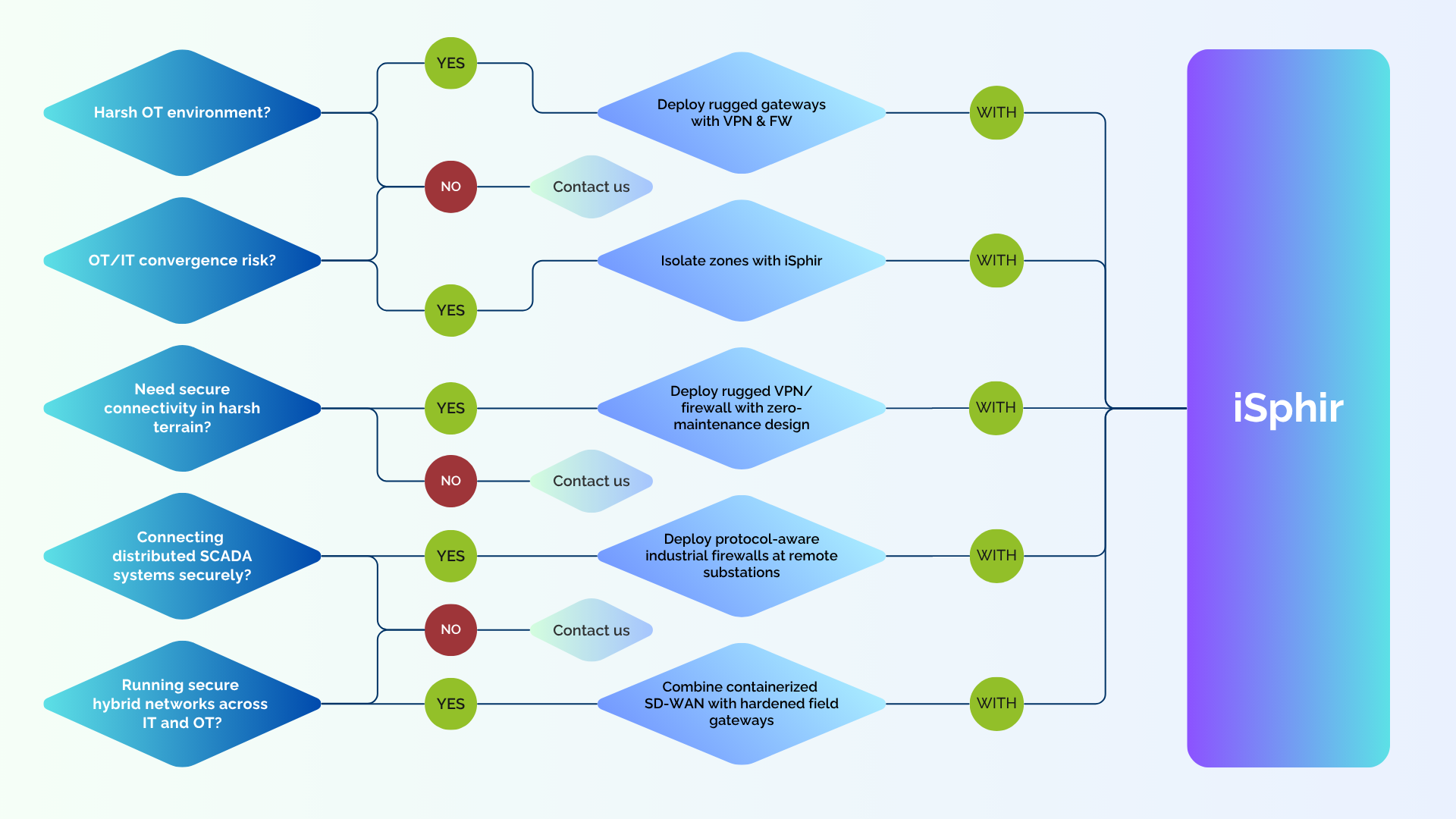
iSphir
Industrial security: hardened gateways for IT/OT and infrastructure

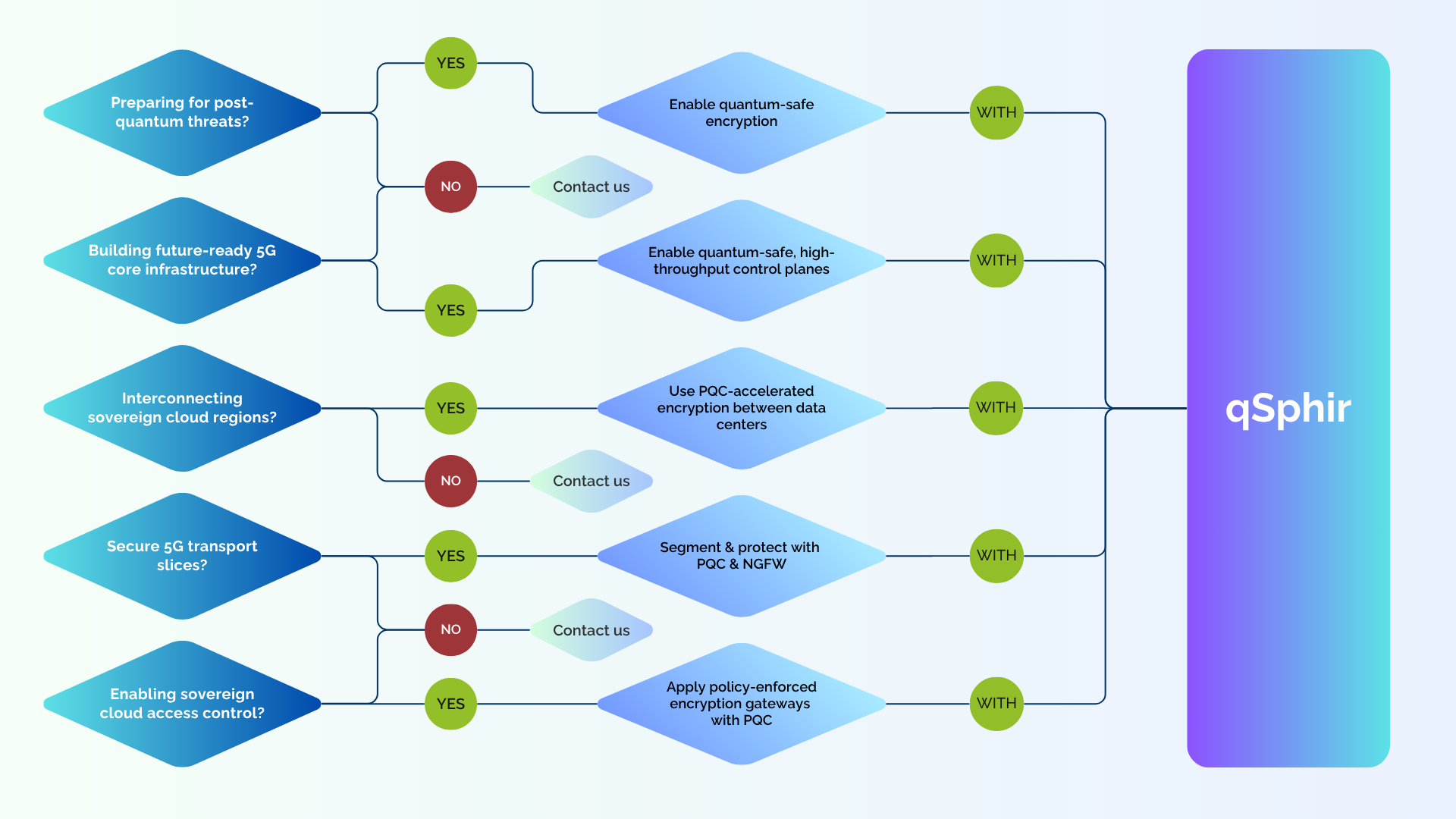
qSphir
Quantum security: ultra-secure encryption for sovereign networks
Meet the Sphir Family: Security Where You Need It
Choosing the optimal Sphir solution depends on your operational environment and security priorities. Each “sphere” is designed to address specific challenges within critical infrastructure and enterprise networks.
Whether you need broad enterprise coverage, hardened industrial resilience, or quantum-resistant encryption, there’s a Sphir solution designed for your unique needs.

Which Sphir solution
fits your needs?
Security isn’t one-size-fits-all, it depends on what you’re protecting, where your infrastructure lives, and what threats you face.
Take this short quiz to get a tailored recommendation based on your environment, challenges, and priorities.
Start the Network Security Check now and find your match in only 5 minutes.
uSphir – Universal Security at the Network Edge
For software-defined, virtualized security.
“Stop stacking hardware. Start scaling security.”
uSphir combines carrier-grade SD-WAN, NGFW, SASE, and routing into a flexible, software-driven platform. It runs on whitebox uCPEs or x86 COTS devices and is fully orchestrated from the cloud.
Use Case: Smart Energy Grid Operator A national energy provider is modernizing its distribution infrastructure with real-time telemetry and remote access. With hundreds of substations and thousands of endpoints, securing every branch and node is a challenge.


iSphir – Intelligent Security for Industrial and Infrastructure Environments
For ruggedized OT and field deployments.
“Security shouldn’t fail when conditions get extreme.”
iSphir is built for resilience and operational certainty in harsh environments. With DIN-rail mountable hardware, extended temperature ranges, and Hardware-secured IPSec, it bridges the gap between IT and OT.
Use Case: National Railway Infrastructure Modernization A major railway operator needs to secure thousands of trackside assets, switches, and signal controllers. Many sites are unmanned, exposed to weather, and rely on legacy interfaces and old unsecured infrastructure.
qSphir – Quantum-Safe Sovereign Network Security
For sovereign, ultra-high security use cases.
“The quantum threat is real. qSphir is ready.”
qSphir delivers the highest levels of encryption with Post-Quantum Cryptography (PQC) and Quantum Key Distribution (QKD) readiness. Its carrier-grade throughput makes it ideal for critical backbone, data center, or control-plane encryption.
Use Case: Sovereign 5G Core and Government Backbone Protection As part of a national cyber defense initiative, a government agency is upgrading its 5G SBA control plane and cloud interconnects. Sensitive routing and orchestration messages must be protected against future quantum decryption.

The Future is Quantum.
The Time is Now.
“Quantum computing may still be emerging but the threat to today’s encrypted data is already here.”
The rise of quantum computing is not just a theoretical concern. Intelligence agencies and advanced attackers are already employing Store Now, Decrypt Later (SNDL) tactics: exfiltrating encrypted data with the intent to break it in the future.
According to Gartner, 65% of large enterprises will face compliance mandates for quantum-safe encryption by 2027.
WHAT’S AT RISK
- Sovereign control planes (5G, government clouds)
- Financial transactions and critical records
- Health, energy, and infrastructure telemetry
HOW QSPHIR PREPARES YOU
- Deploys PQC-ready encryption modules with HSMs now
- Enables QKD ports for future secure key exchange
- Supports hybrid cryptographic migration for minimal disruption
Explore the Right Sphere for Your Network
No two networks are alike and your security shouldn’t be either. Whether you’re securing a rail node in a mountain tunnel, a remote wind turbine farm, or the sovereign control plane of a national 5G network,
Sphir adapts to your reality.
Each industry faces its own security and operational challenges:
- Telecom operators need fast, secure orchestration across thousands of edge locations.
- Utilities and smart grid operators must ensure high availability in harsh, distributed OT environments.
- Government and defense networks demand ultra-high assurance, sovereign supply chains, and protection against future threats like quantum decryption.
aconnic’s modular approach empowers customers to tailor their infrastructure with:
- Granular security zones based on real use cases
- Hardware and software disaggregation to reduce lifecycle costs
- Compliance-friendly deployment patterns based on ENISA, IEC 62443-4-1, and emerging PQC standards
Discover Your Sphir Fit – Tools to Take the Next Step
We don’t just talk about adaptable security. We make it actionable.
An easy-to-follow tool to assess:
- Exposure to edge and OT threats
- Maturity of cryptographic posture
- Readiness for Zero Trust and SASE
Let’s map your architecture together. In this free session, our experts will:
- Review your network & risk posture
- Identify critical gaps
- Propose a modular sphir-based blueprint
The aconnic Promise: Built for Critical Infrastructure
At aconnic, we don’t just integrate security, we secure critical infrastructure.
We engineer our products and solutions specifically for the demands of telecom, energy, government, and industrial environments, where reliability, sovereignty, and scalability are non-negotiable.
From uCPE operating systems to rugged hardware and sovereign encryption platforms, we deliver full-spectrum security innovation, engineered to meet the realities of modern, distributed, and regulated networks. We are the trusted partner for organizations building resilience at the heart of their critical operations.
Let’s build your security sphere!
Please fill out all required fields* of the contact form. We will contact you as soon as possible.